Enabling SDM, preparing router for ssh
user admin privilege 15 secre cisco
ip http server
ip http secure-server
ip http authentication local
ip http timeout-policy idle 600 life 86400 requests 10000
line vty 0 4
privilege level 15
login local
transport input telnet ssh
Supporting ssh
ip domain-name kote.host.ge
hostname central
crypto key generate rsa general-keys
or
crypto key generate rsa general-keys modulus 512
user name and password should be created locally, if no other autentication method was preconfigured
user admin privilege 15 secre cisco
line vty 0 4
login local
transport input telnet ssh
admin
Optional: defining time, during which user must manage to login
central(config)#ip ssh time-out ?
<1-120> SSH time-out interval (secs)
central(config)#ip ssh time-out 2
so in this case 2 secs in not enough:
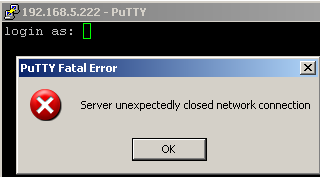
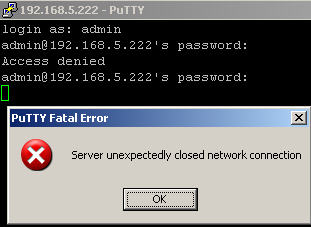
number of unsuccessfull attempts:
entral(config)#ip ssh authentication-retries ?
<0-5> Number of authentication retries
central(config)#ip ssh authentication-retries 2
checking current keys, mypubkey rsa is not the name, it is part of the command
kote# show crypto key mypubkey rsa
deleting old key, in global configuration mode
Router(config)#crypto key ?
decrypt Decrypt a keypair.
encrypt Encrypt a keypair.
export Export keys
generate Generate new keys
import Import keys
pubkey-chain Peer public key chain management
zeroize Remove keys
Router(config)#crypto key zeroize ?
rsa Remove RSA keys
Router(config)#crypto key zeroize rsa
central(config)#crypto key zeroize rsa
% All RSA keys will be removed.
% All router certs issued using these keys will also be removed.
Do you really want to remove these keys? [yes/no]: yes
central(config)#do show crypto key mypubkey rsa
central(config)#
adding ssh
Router1(config-line) # transport input telnet ssh

