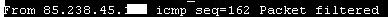ACL
ACL rules:
- sequential order
- once packet is matched - no further comparison
- implicit "deny"
Standard - filtering by source, close to the destination , Extended - by source and DESTINATION, close to the source
Extended access list features- source and destination IP, protocol field in Network layer (tcp, udp), port number at Transport layer (eq telnet, ftp).
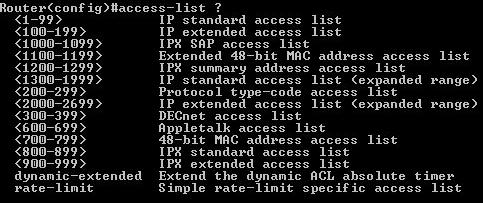
standard 1 - 99 , 1300 - 1999 (expanded range)
extended 100 - 199, 2000 - 2699 (expanded range)
ACLguidelines:
- 1 acl per interface/protocol/direction
- specific tests - at the top
- new entry - at bottom
- to remove single line is possible to remove from named list
access-list 1 - to create standard acl
Router(config)#access-list 1
ip access-group 1 in - to apply
Router(config-if)#ip access-group 1
access-class 1 in - to apply to telnet session,in this case only 172.16.10.3 is permitted:
Lab_A(config)#access-list 50 permit 172.16.10.3
Lab_A(config)#line vty 0 4
Lab_A(config-line)#access-class 50 in
sh access-list 1 - will not show which interfaces have an access list applied.
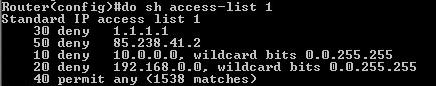
sh ip interface - only this command will tell which interfaces have access lists applied.
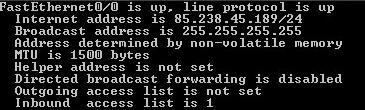
show ip access-list - to view extended ?
show running-config -
effect of the applied acl:
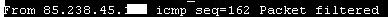
Summary:
access-list - create
ip access-group - apply
access-class - telnet
dlia redaktirovania ACL-ov:
1 nuzhno voitio v rezhim ACL -a
2 vipolnit deistvie, naprimer vstavit stroku:
15 permit ip any any
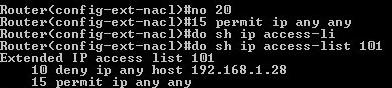
komanda dlia uvelichenia ili umenshenia posledovatelnosti:
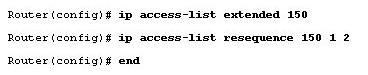
Creation of an acl:
1 choosing list number:
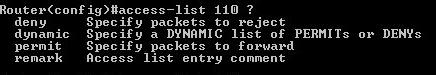
2 choosing action:
3 choosing protocol:
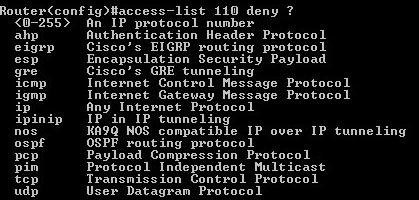
4 choosing source:
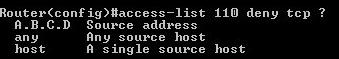
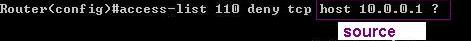
5 - define logical condition
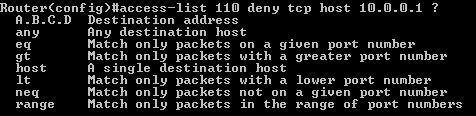
6 - define appropriate port
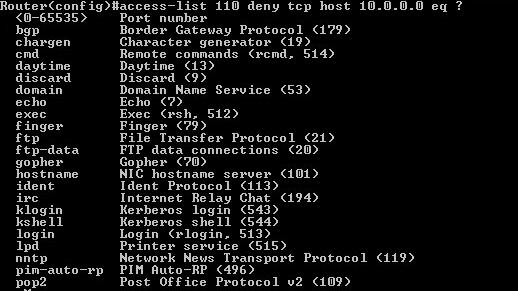
7 - define destination address
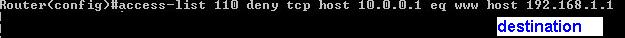
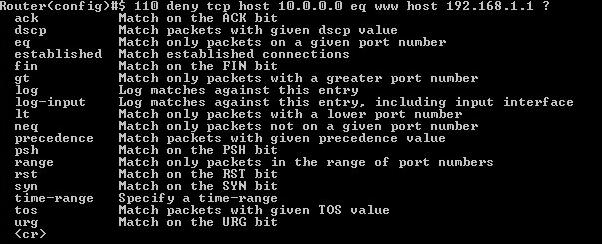
8 - define further specifications
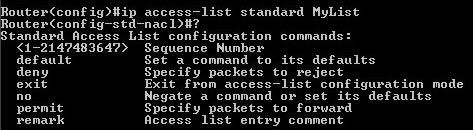
Named access list ip access-list standard MyList - to create named standard acl

Switch Port ACLs
- Port ACLs only to be applied to layer 2 interfaces on switches
- Only inbound lists
- Only named lists
- MAC extended access-lists -only extended use MAC as source and destination
show mac access-group - displays MAC access lists applied to all layer 2 interfaces or the specified layer 2 interface (used on layer 2 switches only)
S1(config)#mac access-list extended Todd_MAC_List
S1(config-ext-macl)#deny any host 000d.29bd.4b85
S1(config-ext-macl)#permit any any
ACL tipps:
- Deny any addresses from your internal networks
- Deny any local host addresses (127.0.0.0/8)
- Deny any reserved private addresses
- Deny any addresses in the IP multicast address range (224.0.0.0/4)
distribute list - unlike access lists is distributed not to interface, but to routing protocol.It does not stop routing advertisments, just controls them.
Reflexive ACL
Reflexive access lists are access rules configured at a router and used to permit IP traffic for sessions originating within your network but to deny IP traffic for sessions originating outside your network.
If an inside user starts a session with a remote address, the reflexive access list will remember thatremote address and allow it to send traffic back to the inside network during the session.
An outside address that has not received a connection request from inside will be blocked.
Example
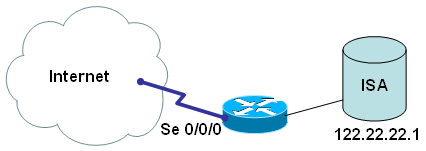
ISA station is only allowed to go out to Internet via 80 port; plus we are collecting these connections for future use - when return traffic is coming back:
Router(config)# ip access-list extended MyACL-forWebOUT
Router(config-ext-nacl)# permit tcp host 122.22.22.1 any eq 80 reflect MyACL-ReturnTraff
Router(config-ext-nacl)# permit udp host 122.22.22.1 any eq 80 reflect MyACL-ReturnTraff
reflect MyACL-ReturnTraff means that it is in pair with MyACL-forWebOUT
Router(config)# ip access-list extended MyACL-ReturnTraff
Router(config-ext-nacl)# evaluate MyACL-forWebOUT
evaluate MyACL-forWebOUT means that we rely on MyACL-forWebOUT access list to allow connections opened by ISA host.
And applying both access lists to corresponding interfaces:
Router(config)# interface S0/0/0
Router(config-if)# ip access-group out MyACL-forWebOUT
Router(config)# interface S0/0/0
Router(config-if)# ip access-group in MyACL-ReturnTraff
Time-based ACL example
Corp#config t
Corp(config)#time-range no-http
Corp(config-time-range)#periodic we?
Wednesday weekdays weekend
Corp(config-time-range)#periodic weekend ?
hh:mm Starting time
Corp(config-time-range)#periodic weekend 06:00 to 12:00
Corp(config-time-range)#exit
Corp(config)#time-range tcp-yes
Corp(config-time-range)#periodic weekend 06:00 to 12:00
Corp(config-time-range)#exit
Corp(config)#ip access-list extended Time
Corp(config-ext-nacl)#deny tcp any any eq www time-range no-http
Corp(config-ext-nacl)#permit tcp any any time-range tcp-yes
Corp(config-ext-nacl)#interface f0/0
Corp(config-if)#ip access-group Time in
Corp(config-if)#do show time-range
time-range entry: no-http (inactive)
periodic weekdays 8:00 to 15:00
used in: IP ACL entry
time-range entry: tcp-yes (inactive)
periodic weekend 8:00 to 13:00
used in: IP ACL entry
Corp(config-if)#
remarks:
R2#config t
R2(config)#access-list 110 remark Permit Bob from Sales Only To Finance
R2(config)#access-list 110 permit ip host 172.16.10.1 172.16.20.0 0.0.0.255
R2(config)#access-list 110 deny ip 172.16.10.0 0.0.0.255
172.16.20.0 0.0.0.255
R2(config)#ip access-list extended No_Telnet
R2(config-ext-nacl)#remark Deny all of Sales from Telnetting
to Marketing