Floating FB sharing byReview Results
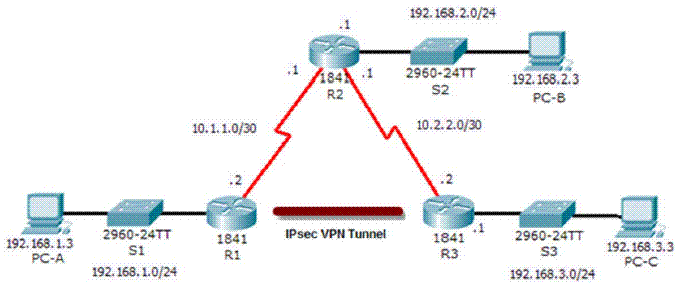
Site-to-Site IPsec VPN using CLI
Site-to-Site vs Remote access
Site-to-site VPNs connect entire networks to each other -- for example, connecting a branch office network to a company headquarters network.
Remote access VPNs connect individual hosts to private networks -- for example, travelers and teleworkers who need to access their company's network securely over the Internet. In a remote access VPN, every host must have VPN client software.The VPN client software encapsulates and encrypts that traffic before sending it over the Internet to the VPN gateway at the edge of the target network. Upon receipt, that VPN gateway behaves as described above for site-to-site VPNs. If the target host inside the private network returns a response, the VPN gateway performs the reverse process to send an encrypted response back to the VPN client over the Internet.
Site-to-Site VPN. Configuring IPsec part
Configiring AL that marks "interesting" traffic:
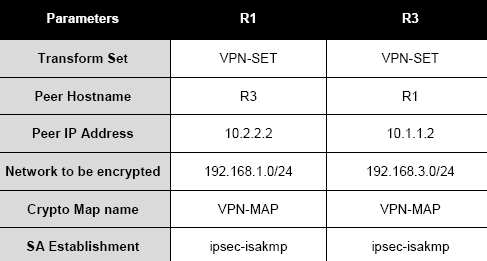
R1(config)# access-list 110 permit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
ISAKMP - Internet Security Association and Key Management Protocol(Phase 1)

R1(config)# crypto isakmp policy 10
R1(config-isakmp)# encryption aes
R1(config-isakmp)# authentication pre-share
R1(config-isakmp)# group 2
R1(config-isakmp)# exit
R1(config)# crypto isakmp key vpnpa55 address 10.2.2.2
map keyword is needed when creating Crypto ACLs, which are used to define the traffic that is protected by IPSec; ISAKMP is enabled by default
R1(config)#crypto ?
dynamic-map Specify a dynamic crypto map template
ipsec Configure IPSEC policy
isakmp Configure ISAKMP policy
key Long term key operations
map Enter a crypto map
R1(config)#crypto isakmp ?
client Set client configuration policy
enable Enable ISAKMP
key Set pre-shared key for remote peer
policy Set policy for an ISAKMP protection suite
R1(config)#crypto isakmp policy ?
<1-10000> Priority of protection suite
R1(config)#crypto isakmp policy 10
Choosing key type and length for encryprion, key length is needed only for AES and is 128 by default
R1(config-isakmp)#?
authentication Set authentication method for protection suite
encryption Set encryption algorithm for protection suite
exit Exit from ISAKMP protection suite configuration mode
group Set the Diffie-Hellman group
hash Set hash algorithm for protection suite
lifetime Set lifetime for ISAKMP security association
no Negate a command or set its defaults
R1(config-isakmp)#encryp ?
3des Three key triple DES
aes AES - Advanced Encryption Standard
des DES - Data Encryption Standard (56 bit keys)
R1(config-isakmp)#encryp aes ?
128 128 bit keys.
192 192 bit keys.
256 256 bit keys.
R1(config-isakmp)#encryp aes
Encryption part
Configuring pre-shared keys is the easiest. With pre-shared keys, the same key (symmetric) is used on both peers to perform the device authentication.
Pre-shared keys, symmetric or asymmetric, commonly are used when you have a small number of devices with which you need to establish IPsec tunnels, however, pre-shared keys scale poorly and thus digital certificates are used to solve the device authentication scalability issues. The one advantage that pre-shared keys have over certificates, especially symmetric pre-shared keys, is that they are simple to set up on the two IPsec peers.
link
Cisco routers support three methods of authenticating IPsec devices (peers): Pre-shared keys, RSA encrypted nonces, and RSA signatures (digital certificates).
Authentication part
Router(config-isakmp)#authentication ?
pre-share Pre-Shared Key
rsa-encr Rivest-Shamir-Adleman Encryption
rsa-sig Rivest-Shamir-Adleman Signature
Diffie-Hellman (DH) groups determine the strength of the key used in the key exchange process. Higher group numbers are more secure, but require additional time to compute the key.
- DH Group 1: 768-bit group
- DH Group 2: 1024-bit group
- DH Group 5: 1536-bit group
Both peers in a VPN exchange must use the same DH group, which is negotiated during Phase 1 of the IPSec negotiation process.
R1(config-isakmp)#group ?
1 Diffie-Hellman group 1
2 Diffie-Hellman group 2
5 Diffie-Hellman group 5
R1(config-isakmp)#group 2
PSK and peer IP address, IP address is peers's IP , bypassing router R2 in our case
R1(config)#crypto isakmp key ?
WORD The UNENCRYPTED (cleartext) user password
R1(config)#crypto isakmp key MyVPNPassword ?
address define shared key with IP address
R1(config)#crypto isakmp key MyVPNPassword address ?
A.B.C.D Peer IP address
R1(config)#crypto isakmp key MyVPNPassword address 10.2.2.2 ?
A.B.C.D Peer IP subnet mask
R1(config)#crypto isakmp key MyVPNPassword address 10.2.2.2
Configuring the ISAKMP Phase 2 properties
Configuring an IKE Phase 2 Tunnel
Router(config)#crypt ipsec ?
client Configure a client
df-bit Handling of encapsulated DF bit.
fragmentation Handling of fragmentation of near-MTU sized packets
nat-transparency IPsec NAT transparency model
optional Enable optional encryption for IPSec
profile Configure an ipsec policy profile
security-association Security association parameters
transform-set Define transform and settings
Define transform sets, for the IPsec encryption, hashing, and other choices.
Router(config)#crypt ipsec transform-set ?
WORD Transform set tag
AH-MD5-HMAC - Authentication Header with the MD5 (HMAC variant)
HMAC - Hash-based Message Authentication Code
SHA - Secure Hashing Algorithm
COMP-LZS - IP compression algorithm
ESP - Encapsulating Security Payload. An IPSec protocol that provides both data integrity and confidentiality
SEAL - Software Encryption Algorithm
specifying the encryption algorithm
ESP-NULL - ESP transform that provides no encryption and no confidentiality.
Router(config)#crypt ipsec transform-set MySet ?
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
comp-lzs IP Compression using the LZS compression algorithm
esp-3des ESP transform using 3DES(EDE) cipher (168 bits)
esp-aes ESP transform using AES cipher
esp-des ESP transform using DES cipher (56 bits)
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-null ESP transform w/o cipher
esp-seal ESP transform using SEAL cipher (160 bits)
esp-sha-hmac ESP transform using HMAC-SHA auth
specifying the hashing algorithm
Router(config)#crypt ipsec transform-set MySet esp-3des ?
ah-md5-hmac AH-HMAC-MD5 transform
ah-sha-hmac AH-HMAC-SHA transform
comp-lzs IP Compression using the LZS compression algorithm
esp-md5-hmac ESP transform using HMAC-MD5 auth
esp-sha-hmac ESP transform using HMAC-SHA auth
R1(config)# crypto ipsec transform-set MySet esp-3des esp-sha-hmac
now we bind already created MySet to some map (MyMap)
Router(config)#crypto map MyMap 10 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
Router(config-crypto-map)#se
Router(config-crypto-map)#set transform-set kkk
ERROR: transform set with tag "kkk" does not exist.
Router(config-crypto-map)#set transform-set MySet
defining other options, 101 - is an predefined ACL number
R1(config-crypto-map)# description VPN connection to R3
R1(config-crypto-map)# set peer 10.2.2.2
R1(config-crypto-map)# match address 110
R1(config-crypto-map)# exit
binding the VPN-MAP crypto map to the outgoing Serial 0/0/0 interface
R1(config)# interface S0/0/0
R1(config-if)# crypto map VPN-MAP
checking with sh crypto map command:
Router#sh crypto map
Crypto Map "MyMap" 10 ipsec-isakmp
Peer = 10.2.2.2
Extended IP access list 110
access-list 110 permit ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.25
5
Security association lifetime: 4608000 kilobytes/3600 seconds
PFS (Y/N): N
Transform sets={
MySet,
}
Interfaces using crypto map MyMap:
Crypto Map "VPN-MAP" 10 ipsec-isakmp
WARNING: This crypto map is in an incomplete state!
(missing peer or access-list definitions)
No matching address list set.
Security association lifetime: 4608000 kilobytes/3600 seconds
PFS (Y/N): N
Transform sets={
MySet,
}
Interfaces using crypto map VPN-MAP:
Router#




